29C3 - Version 1.9
| Referenten | |
|---|---|
|
|
djb |
|
|
Jean-Philippe Aumasson |
|
|
Martin Boßlet |
| Programm | |
|---|---|
| Tag | Day 3 - 2012-12-29 |
| Raum | Saal 4 |
| Beginn | 21:45 |
| Dauer | 01:00 |
| Info | |
| ID | 5152 |
| Veranstaltungstyp | Vortrag |
| Sprache der Veranstaltung | englisch |
| Feedback | |
|---|---|
|
Haben Sie diese Veranstaltung besucht? Feedback abgeben |
Hash-flooding DoS reloaded: attacks and defenses
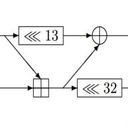
At 28C3, Klink and Waelde showed that a number of technologies (PHP, ASP.NET, Ruby, Java, Python, etc.) were vulnerable to the decade-old hash-flooding DoS attacks. The vulnerability was then often fixed by adopting stronger hash functions and "randomizing" them.
We show that it's not enough, at least for systems relying on "MurmurHash" or on Google's "CityHash64", by presenting powerful "universal multicollision" attacks for those functions. We will present demos showing how to exploit these attacks to DoS a Ruby on Rails application, as well as the latest Java OpenJDK7. We also describe a vulnerability of Python's new randomized hash, allowing an attacker to easily recover the 128-bit secret seed. As a reliable fix to hash-flooding, we introduce SipHash, a family of cryptographically strong keyed hash function competitive in performance with the weak hashes, and already adopted in OpenDNS, Perl 5, Ruby, and in the Rust language.
