Version 1.7 a new dawn
lecture: Mining for Bugs with Graph Database Queries
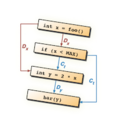
While graph databases are primarily known as the backbone of the modern dating world, this nerd has found a much more interesting application for them: program analysis. This talk aims to demonstrate that graph databases and the typical program representations developed in compiler construction are a match made in heaven, allowing large code bases to be mined for vulnerabilities using complex bug descriptions encoded in simple, and not so simple graph database
queries.
This talk will bring together two well known but previously unrelated
topics: static program analysis and graph databases. After briefly
covering the "emerging graph landscape" and why it may be interesting for hackers, a graph representation of programs exposing syntax, control-flow, data-dependencies and type information is presented, designed specifically with bug hunting in mind. Our open-source program analysis platform Joern (http://mlsec.org/joern/) is then introduced, which implements these ideas and has been successfully used to uncover various vulnerabilities in the Linux kernel. Capabilities and limitations of the system will then be demonstrated live as we craft queries for buffer overflows, memory disclosure bugs and integer-related vulnerabilities.
Info
Day:
2014-12-28
Start time:
20:35
Duration:
01:00
Room:
Saal G
Track:
Security & Hacking
Language:
en
Links:
Feedback
Click here to let us know how you liked this event.
Concurrent events
Speakers
| fabs |