27C3 - Version 1.6.3
27th Chaos Communication Congress
We come in peace
| Speakers | |
|---|---|
|
|
Jeroen Massar |
| Schedule | |
|---|---|
| Day | Day 4 - 2010-12-30 |
| Room | Saal 1 |
| Start time | 16:00 |
| Duration | 01:00 |
| Info | |
| ID | 4301 |
| Event type | Lecture |
| Track | Society |
| Language used for presentation | English |
| Feedback | |
|---|---|
|
Did you attend this event? Give Feedback |
How the Internet sees you
demonstrating what activities most ISPs see you doing on the Internet
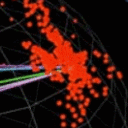
On the Internet one tends to think that one is pretty much safe from poking eyes. Taps in most countries can only be established after a judge has issued a warrant, thus upto such a tap is succesfully deployed one might think one is pretty much in the clear.
Most ISPs though actually employ a toolset comprising one of various NetFlow, IPFIX or sFlow protocols to do trend monitoring, billing and of course, the ability to try and establish which connections a certain IP address is making.
During the CCC conference we will monitor the CCC network with NetFlow, collecting and directly anonimizing this information on IP basis. We will map a couple of well-known websites/trackers to a private IP range and preserving these mappings, while anonimizing the rest of the IP addresses, thus your anonimity is safe and please be yourself while using the network. Flow data will not be stored, thus we won't be able to go back and re-analyze the information.
As a collector/analyzer we will be using the Anaphera tool by IBM Zurich Research Laboratory [1]. This tool is used in IBM datacenters and by customers of IBM worldwide for detecting malicious/unknown network traffic, traffic trending, anomaly detection, growth prognosis and billing.
We'll be explaining the intriciate parts about NetFlow, IPFIX and sFlow, what the technologies are and how they work, hopping briefly in the big difference with taps and what they could see when they are deployed and also what we don't see now and what gets lost in the noise.
We will be showing you what information and details can be taken from a flow based tool, so that you know what can be seen by ISPs around the world.
