26C3 - 26C3 1.15
26th Chaos Communication Congress
Here be dragons
| Referenten | |
|---|---|
|
|
Mathias Payer |
| Programm | |
|---|---|
| Tag | Day 4 - 2009-12-30 |
| Raum | Saal2 |
| Beginn | 11:30 |
| Dauer | 01:00 |
| Info | |
| ID | 3515 |
| Veranstaltungstyp | Vortrag |
| Track | Hacking |
| Sprache der Veranstaltung | englisch |
| Feedback | |
|---|---|
|
Haben Sie diese Veranstaltung besucht? Feedback abgeben |
secuBT
Hacking the Hackers with User-Space Virtualization
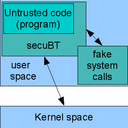
In the age of coordinated malware distribution and zero-day exploits security becomes ever more important. This paper presents secuBT, a safe execution framework for the execution of untrusted binary code based on the fastBT dynamic binary translator.
In the age of coordinated malware distribution and zero-day exploits security becomes ever more important. This paper presents secuBT, a safe execution framework for the execution of untrusted binary code based on the fastBT dynamic binary translator.
secuBT implements user-space virtualization using dynamic binary translation and adds a system call interposition framework to limit and guard the interoperability of binary code with the kernel.
Fast binary translation is a key component to user-space virtualization. secuBT uses and extends fastBT, a generator for low-overhead, table-based dynamic (just-in-time) binary translators. We discuss the most challenging sources of overhead and propose optimizations to further reduce these penalties. We argue for hardening techniques to ensure that the translated program can not escape out of the user-space virtualization.
An important feature of secuBT is that only translated code is executed. This ensures code validity and makes it possible to rewrite individual instructions. The system call interposition framework validates every system call and offers the choice to (i) allow it, (ii) abort the program, (iii) redirect to an user-space emulation.
