27C3 - Version 1.6.3
27th Chaos Communication Congress
We come in peace
| Referenten | |
|---|---|
|
|
Kay Hamacher |
|
|
Stefan Katzenbeisser |
| Programm | |
|---|---|
| Tag | Day 3 - 2010-12-29 |
| Raum | Saal 2 |
| Beginn | 12:30 |
| Dauer | 01:00 |
| Info | |
| ID | 4055 |
| Veranstaltungstyp | Vortrag |
| Track | Science |
| Sprache der Veranstaltung | englisch |
| Feedback | |
|---|---|
|
Haben Sie diese Veranstaltung besucht? Feedback abgeben |
Terrorists Win - Exploiting Telecommunications Data Retention?
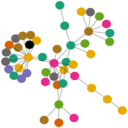
Telecommunications data retention (TDR) has become a reality in most Western countries. Protagonists claim that the collection of massive amounts of data on the communication behavior of all individuals within a country would enable law enforcement agencies to exploit patterns in the stored data to uncover connections between suspects.
While this is obviously true for investigations after an incident happened, there is up to now no critical and sound assessment publicly available that evaluates whether TDR brings any pro-active benefits for the above mentioned, justified purposes.
In this talk we give for the first time a critical assessment of the power of TDR based on methods from information theory. To this end we have employed agent based simulations, which mimic the communication behavior of a large community including a dark-net of alleged suspects. The structure and statistics of our telecommunication simulation, which drive the dynamics of telephone calls and simulated TDR data, were generated according to known statistics of real-world telecommunications networks.
Hiding in the unavoidable noise seems to be a passive strategy for terrorists to circumvent pro-active detection. This stems from a "needle in the haystack"-problem, that arises due to the small number of conspirators compared to the number of other participants.
In particular situations and with adopted strategies suspected terrorists might be able to eventually exploit TDR for their purposes and take an active approach to hiding in the crowd. Such TDR exploits would lower the probability of detection by law enforcement agencies and render TDR a potential security threat. Again, we use our simulations and our analysis procedure to assess this problem.
